So is anyone here trying to recoup their fees?
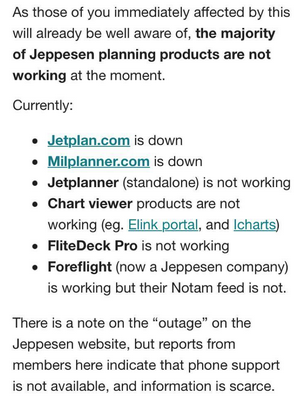
Some parts of programs are working. Like updates or notams for foreflight are not
ForeFlight NOTAM feed doesn’t work for few days (I believe from November 1st).
That yahoo URL has no relevant content so I googled around…
Found this
However, it does appear that Jeppesen is dealing with a ransomware attack, meaning they have a choice of paying a ransom to restore service, or find an alternate way of providing service. Much as the impact of the outage will weigh heavy on some operators, our thoughts are with Jeppesen – not a nice situation to be in at all.
Given the situation it seems lilkely that the outage may continue for some time yet.

I guess that if they have their phones on VOIP and run that in-house, then messing up their servers would stop phones working too.
Cleaning up after a ransomware attack is very painful and expensive, even if the scope was limited. These things are a nightmare, and Erasmus was right about prevention vs. cure. Unfortunately the bad guys are clever, and they only have to succeed once – you have to successfully block them 1000s of times a day.
eurogaguest1980 wrote:
Unfortunately the bad guys are clever,
… as they’ve started to attack not just the primary data but the secondary (backup, snapshots, etc.) as well. Makes it even more painful.
I wonder how many of these attacks were actually very simple, and made possible by dumb IT practices?
There was some big hack here in the UK (possibly the NHS?) which got blamed on the use of WinXP, but actually it was somebody having set up an RDP (Remote Desktop) server on some internal LAN and exposed the RDP login to the outside world. It’s been known for as long as RDP has been around (20 years?) and before that re earlier remote working solutions like PC/Anywhere, that this is dumb, RDP has had easy and widely known back doors since for ever, and nobody should be doing this unless they use a VPN. RDP, WinXP, etc, are as safe as the VPN is strong. Same thing applies to practically all remote access methods. Every time I hear somebody telling me XP is insecure, I know they are talking complete BS.
One is still hoping that the VPN terminator (the VPN router, typically) has no back doors, but that is a much smaller attack surface than having some LAN accessible entirely via an open port.
I am finishing off an industrial product which has a simple HTTP server (which I also wrote, having found the various open source ones just over-complicated junk) for browser based config. Obviously this is intended for local LAN config only; only an idiot will put an “IOT” box (“IOT” = any embedded product with a LAN interface, and a required bit of BS on your CV, along with “full stack”) on an open port, visible to any chinese or russian hacker. But lots of people do exactly that! Then people tell me if I make that server HTTPS (which is a vast amount of extra code; impractical for other reasons too) it will be much safer  You have to know a bit about IT to see the utter irony of that.
You have to know a bit about IT to see the utter irony of that.
So companies pay 1k+ per day to IT nerds (whose CV has all the right trendy verbiage) to set up their systems but they just get back doors left there. Also nearly all IT systems are completely undocumented because that it how you get job security.
Lots of people keep backups on the same server – e.g. here. I expect that French pilot shop knew little about IT.
The problem this sort of thing causes is that you cannot really send emails with attachments to many firms now. Attachments are an attack vector which is almost impossible to block. EuroGA PMs cannot have attachments for this reason. But Jeppesen never read emails anyway 
Peter, re: old software – the reason it is even more insecure, because it has many more well-documented zero-day (i.e. unpatched) vulnerabilities, unlike the modern OS. So if you stay patched, you are more secure.
Re: clear-text protocols – the reason people drop those is they are much more easier to intercept, so in modern what they call “zero-trust” world (meaning there is an assumption that your network has already been compromised), that creates a very substantial attack surface.
re: InfoSec in general – the goal is not to become absolutely impenetrable (that is impossible). The goal is in that old joke that you need to run faster than your mate, so the lion is going to catch up with him, not you; so in other world make your network less hackable to that the hacker realises that it makes it impractical to hack you, better to change to easier target… And that is why one gets security scans regularly and external audits as well – to ensure you are not an easy target.
arj1 wrote:
… as they’ve started to attack not just the primary data but the secondary (backup, snapshots, etc.) as well. Makes it even more painful.
Indeed, the really clever criminals get in and do some homework before they strike. They might be there for months understanding the storage and backup systems. Very few organizations have a backup from a year ago that will be useful. Very few pen testers fail to get “admin” access once they get into the softer internal “trusted” network.
There are lots of well-known industry best practices that can reduce the risk, but it takes an investment in time and resources to get them implemented, something that a lot of organizations don’t allocate to this. So they get attacked.
Peter wrote:
Then people tell me if I make that server HTTPS (which is a vast amount of extra code; impractical for other reasons too) it will be much safer You have to know a bit about IT to see the utter irony of that.
As long as you are not exchanging sensitive info, nothing wrong with http.
That wasn’t my point  Almost nobody “gets in” by decrypting stuff. But that’s off topic – embedded is a different thing.
Almost nobody “gets in” by decrypting stuff. But that’s off topic – embedded is a different thing.
Jeppesen’s biggest issue is probably that most of their employees are incompetent, which makes it easy to do a trojan attack.
We get these at work almost daily, but the person opening the emails is smart, plus we use a ~25 year old email program which doesn’t load HTML emails, 3rd party links of any kind, and doesn’t touch attachments unless you click on them. But running that kind of system requires smart people.
A lot of organisations hope to deal with this by using services which load the attachment, virus check it, store it on their server, and forward the email onto you with the attachments replaced with links to that server. That’s what the UK CAA does for example. But these are trivial to bypass if the person in your office clicks on everything.